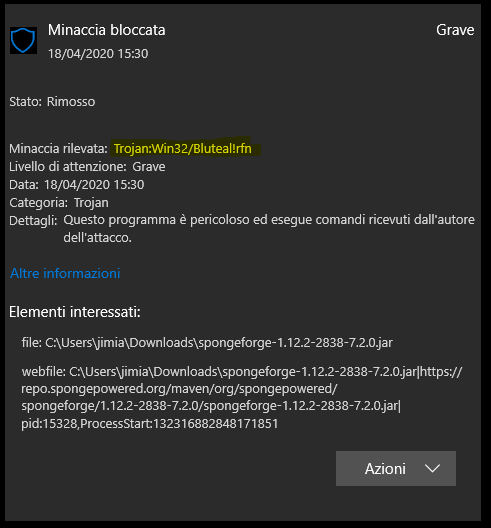
It’s a sunny day here in Italy, everything goes well, besides the current situation, and I’m ready to do stuffs with Sponge. So I write a bunch of code, I run the test server aaaaand… “Windows Defender found a virus”. Oh crap, what could it be? Well, I don’t know why, I don’t understand why it would, but appearently Windows Defender thinks that the SpongeForge jar contains a virus  . Yes, I know, I should get a decent antivirus, but why it suddendly did this? Again, is just from today, yesterday it was all fine
. Yes, I know, I should get a decent antivirus, but why it suddendly did this? Again, is just from today, yesterday it was all fine 
And I know I shouldn’t worry about it, but I’m just curious on why it detects like this
It maybe activity that is occuring within sponge due to a plugin. What plugins do you have and what does your plugin do?
It throws the alert just by downloading the jar. So even the jar itself in the downloads folder throws the alert  The test server has currently the latest stable sponge forge jar and a plugin I’m making that for now the only thing it does is saying “Hello” on the console when an event occur, that’s it
The test server has currently the latest stable sponge forge jar and a plugin I’m making that for now the only thing it does is saying “Hello” on the console when an event occur, that’s it
I can replicate it, it means SpongeForge has been reported as a virus to the windows defender. Im not sure how it gets reported on Windows defender, I know some virus scanners automaticly flag files as viruses if abnormal activity is detected, some will be more advanced.
Oddly enough, Sponge Vannila (which shares a lot of code with SpongeForge) does not get detected. This probably means that if it is automaticly flagged, then its a mod that has been interacting with SpongeForge (easy to do even accidently) to act as a virus on peoples servers.
So does this mean I should actually worry about it?
By the way it does with the 7.2.1 RC builds too, but not with the last 7.1.1 build (1.12.2-2838-7.1.11-RC4007)
Nope you shouldnt worry about it, Spongepowered is open source, if you are worried then you can download and compile the version from GitHub (which shows all code, so any viruses would be displayed on the Github page which the public would have picked up (yes there are people such as myself who read code)).
My guess with Windows defender is it checks the instance of the file, to make sure it doesnt detect a incorrect file as the virus file.
Good evening,
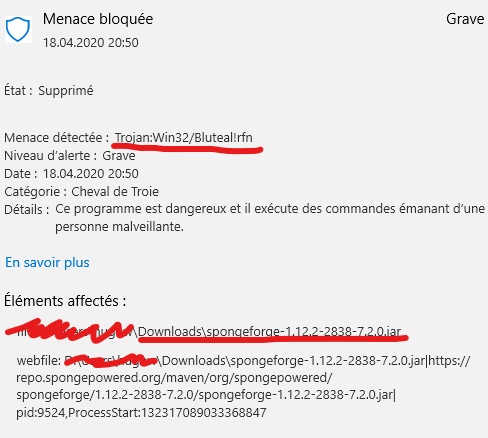
I faced the same problem as @Francesco_Jimi. Windows defender told me that SpongeForge contains a virus.
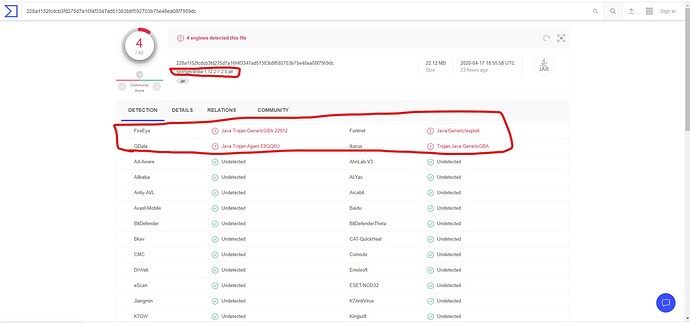
I checked the SpongeVanilla version with an online virus checker and it told me the same as Windows defender !
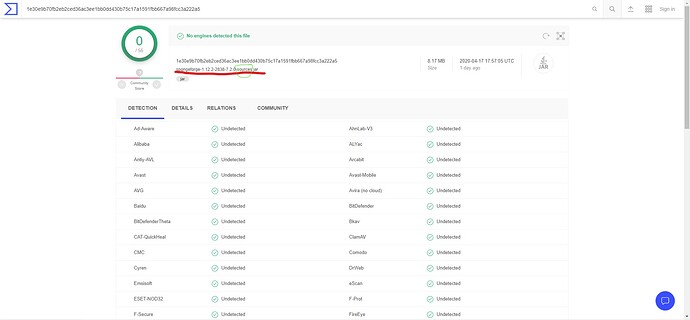
I also checked the spongeForge “source” jar and this time no virus was found.
The online virus checker I used is : VirusTotal
I think the threat might be real, although I hope the virus is a false positive.
Please consider my message with the utmost importance !
Best Regards.
The “source” jar has only the source code within, something windows defender will not check, instead it checks the compiled code. Thats why windows defender (or your online one) isnt picking it up on source . Interesting that the online one picks up compiled spongeforge
@dualspiral What do you think is happening? Also wouldnt this harm the downloading on sponge forge? (As browsers such as Google chrome have hooks into anti viruses to prevent the downloading of known viruses)
I’m not an AV programmer and I have no idea why Sponge is tripping up now. Rest assured Sponge does not contain a virus or trojan.
We have checked our own downloads and they are as we expect - clean. In most AVs that have false positives, we’re seeing that PacketPhaseUtil.class is the problem - and that’s not changed for some time. All “trojan” types that are being flagged are those that indicate that the heuristics engines have picked it up - that is, the predictive part of the AV engines - it’s important to note that detections are not detecting anything specific, they just are saying “hey, maybe it looks like something’s a bit off”. Don’t forget, Sponge does bytecode transformation at launch - it’s injects itself into Minecraft and changes how it runs. It’s a mod! I’m surprised this hasn’t happened sooner!
The best I can suggest is:
- Make sure you ALWAYS download Sponge from our download sites ONLY - https://spongepowered.org/downloads. We cannot guarantee the authenticity of anything downloaded from elsewhere.
- Check that the SSL certificate is valid on our websites and that the connection is secure, if there is no padlock, do not trust the site. On Firefox, I see this:
It’s similar for Chrome. - If you trust us enough, whitelist the Sponge jar in your AV. I personally know it’s fine, but it still pays to keep your wits about you. This is the internet people!
- Report the Sponge JAR to your AV provider using any tools for reporting false postives - the do rely somewhat on user reports to patch over thes false positives.
I have reported it to Avast but got no response - though that is probably because they don’t give a response and someone said that after I submitted it, it was fine. Based on this, people should do the same for their AV provider. How they do that is an exercise for the reader.
For those that are curious, as I am, although I do not know very much about the subject:
Modern Antivirus no longer looks merely for specific exploits, but rather mostly they use very advanced algorithms that detect code in data and detect if the code loads more code. Between that and a few other checks, the antivirus will flag that code as dangerous.
What I do not know much about is how this translates between languages. From my understanding the algorithms that do the analysis are pretty abstract and based more in mathematics, so it seems like it would work across several different languages.
But then again I have no idea how antivirus works.
Nothing to worry about I guess.
I always get some files detected as a threat weekly. xD
This is a very wrong and dangerous statement to make.
The files, binaries and text embedded within a JAR are both executable and in other cases simply code that in some instances isn’t even “compiled” until runtime. The same is true of the source code. Modern sandboxing has eliminated the obfuscation of malicious payload inside source.
Defender and other modern malware tools check the presence of items resident in text, binaries via SHA hashing, the memory address in use, process IDs (pids), the processes accessing areas of the file system and memory addresses they don’t have any need to (using heuristic and profile methods along with AI|ML)…etc. There’s very little to hide from modern malware scanners. This is why REAL l337 h@><ors leverage tried and true social engineering methods such as Phishing, Smishing etc. It’s much easier to bypass a human firewall than it is a machine one.
So to suggest that “it’s nothing to worry about” purely because “the source jar only has source code in it” is frankly reckless. It’s also flat out wrong.
I have detected numerous identified trojans inside Jars that windows and other OS Malware scanners catch as malicious. The class path itself has references and in some case actual jar files from other sources which the target App depends on to function.
One such payload was present in a recent Sponge distro, which was added as a dependency by a developer who didn’t fully research the sources they were import to their API.
So, even when you obtain a file , particularly Java which is among the easiest attack vectors on the planet, from a “Trusted Source” always do your due diligence.
False positives absolutely do happen, but the risk of ignoring it is much greater than the time spent just making doubly sure.
If you can provide details of this we would appreciate it.
In general, if you get Sponge implementations from our official download site, it should be safe. We can’t vouch for any third party distributions or plugins, so caveat emptor applies.